Blogpost
Security in card-based payment
Meet our authors
Reference items
Expert EN - Dominik Siebert

Managing Partner
Dominik
Siebert
Dominik Siebert is Managing Partner at CORE and has extensive experience in complex transformation projects in the financial industry, from strategic conceptualisation to implementation management....
Read moreDominik Siebert is Managing Partner at CORE and has extensive experience in complex transformation projects in the financial industry, from strategic conceptualisation to implementation management. At CORE, Dominik focuses on projects for the development and strategic positioning of digital payment solutions.
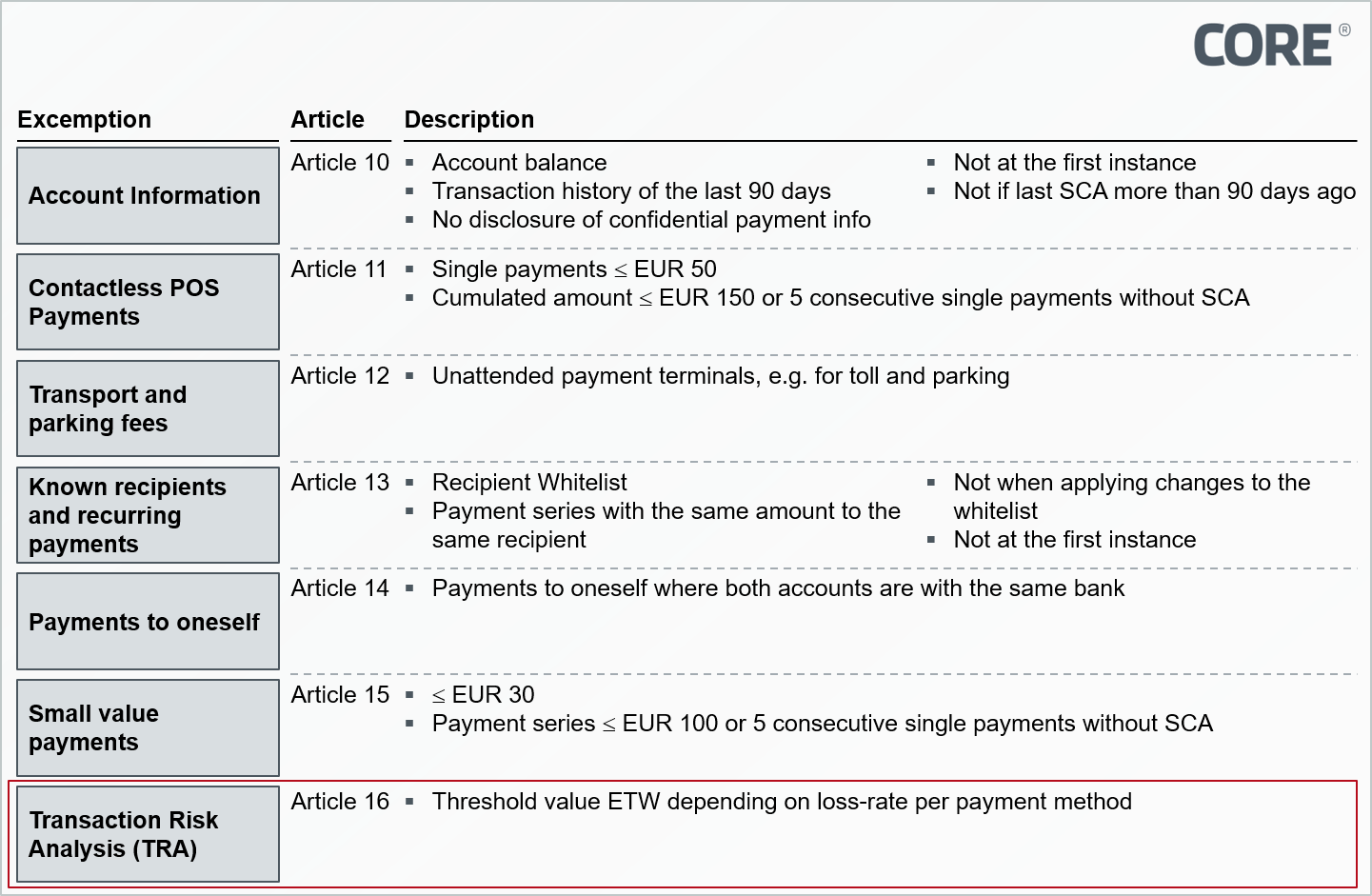 Figure 1: Exemptions to the use of strong customer authentication
Figure 1: Exemptions to the use of strong customer authentication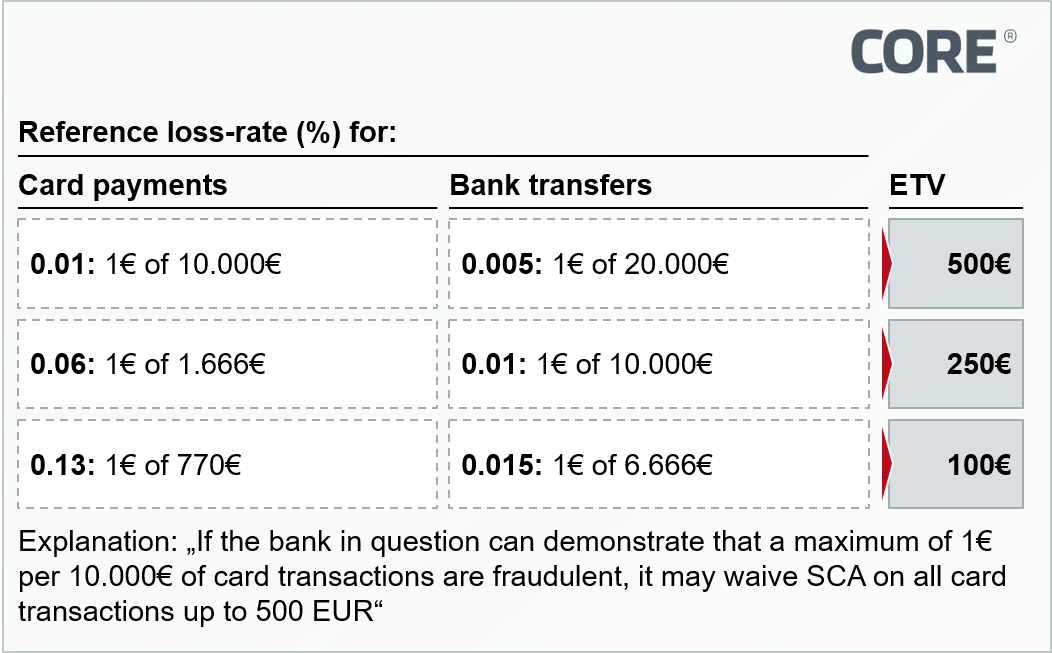 Figure 2: ETV depending on loss rate and payment instrument
Figure 2: ETV depending on loss rate and payment instrument

