Identity and Security – The Empowerment of the User through Technological Emancipation
KEY FACTS
-
User identity data highly exposed in digital space
-
Technological perimeter security paradigms used nowadays are insecure and vulnerable
-
There is currently little pressure to change security paradigms
-
Approaches for technological emancipation by individual market participants and direct technological requirements on the part of the regulator
-
Empowering users by changing technologies and processes, and thereby creating sovereignty over their data in digital space
Fundamental Uncertainty Surrounding Identity Data
Users leave behind extensive traces when using apps and internet-based services. In contrast to the analog world, these generally remain available in the form of data and are analyzed and used by various service providers for a range of purposes. This process is usually legitimated by the business relationship between users and service providers. In most cases, this is used for targeted advertising. Some of the information and services also provide simplification for users, e.g. in the form of additional information about routes or delays.
The underlying data belongs to the digital identity of the user, or can be attributed to it (a fact that the user must be made aware of); in other words: Users make data accessible – also meaning that this data can be attributed to their identity whether they desire so or not. The user and their data are just as much a product as the platforms and services provided by the service provider.
However, there are other illegitimate or illegal facets of data usage in addition to the forms of the agreed use of user data. There are gray areas in terms of anonymized disclosure of data to third parties or the further pursuit of digital “zombie users” (accounts that are no longer used and have not been deleted). Furthermore, despite the user objecting to data collection, e.g. if they opt to disable geolocationing, all sources will continue to be collected by the provider.
A breach in the integrity of networks with the aim of stealing data is to be distinguished from this – be the networks corporate networks, databases or home computers belonging to consumers. These breaches are partly directly related to software (and hardware) security holes; they sometimes gain access through the seizure of user access data, which poses a major risk due to its simplicity and frequent reuse. A forgotten account or an easy-to-hack password in digital space is the equivalent of showing your ID on the street or signing a slip of paper without checking it in the analog world. Just one breach is enough to carry out extensive analyzes on the behavior and preferences of users.
The consequences for the user are incalculable. The data allows many groups to draw conclusions. This starts with persistent, personalized advertising, and extends to no-fly lists and adjusting credit scores. Moreover, the user loses complete control over their data, learning nothing about the information and its origin, nor about how it is stored, analyzed and used. The only thing they notice is that they are no longer able to fly or that they are given a higher interest rate on a loan.
Regulatory authorities have hitherto pursued a purely legal approach by sanctioning unauthorized transfer of data. The general uncertainty surrounding technologies often used to store, analyze and use the data has not been a factor.
Users retain full control over their personal data with VERIMI
VERIMI is designed as a central and cross-industry platform. Users register once and can then use the digital services and products of the connected partners. VERIMI also offers users the simple option of transferring customer data already stored on a partner’s platform. The main advantage of VERIMI is that users retain full control over their own data. Using settings on the platform, they can decide for themselves which personal data they want to share with which partner. Approvals once granted can be revoked at any time. VERIMI is designed as a central platform in the first release but will be converted to a decentralized model with the appropriate degree of mature technologies.
With the integration of VERIMI, partner companies benefit from a secure and simple way of addressing and retaining customers digitally in accordance with the General Data Protection Regulation (GDPR). VERIMI also delivers secure identities to connected partners, reducing transaction breakups and payment defaults. In addition, VERIMI is continuously acquiring new partners and customers, thereby increasing the platform’s reach and relevance. VERIMI is developed as a platform open for all industries and branches, which makes it easy for companies to integrate the green VERIMI buttons comfortably into existing online offers.
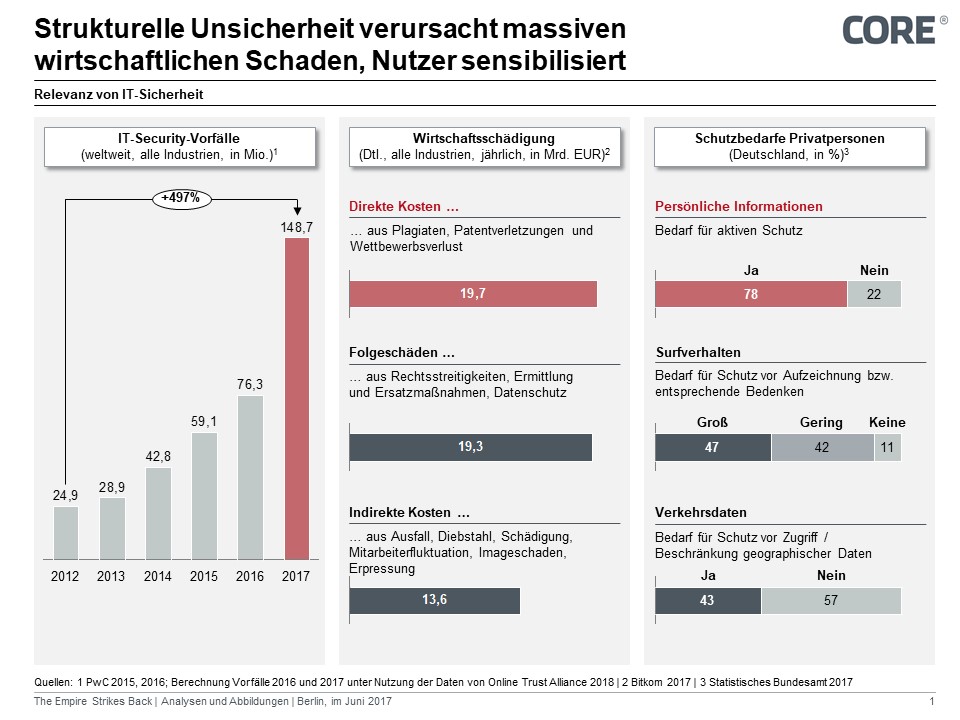
Figure 1: Structural Uncertainty Causes Massive Economic Damage, Sensitizing Users
Low Inherent Change Vector
The parties involved have little intrinsic motivation to change this situation. Influencing user behavior is rarely successful, as there are few alternatives available, and avoiding the use of apps and services would lead to a loss in quality of life and digital benefit for social relationships.
As far as service providers are concerned, there are a few companies that have an interest in the security of user data and thus ensuring the highest level of security. For many companies, however, the acquisition and use of data is part of the DNA of their business model. And for good reason – from the perspective of service providers – it is difficult for the user to adjust the settings of their smartphone to make it data protection friendly. The smartphone’s authorization settings are hardly useful in helping with this issue, e.g. they do not prevent access to unique access numbers such as the IMEI or MAC address.
After all, the prevailing technology-architecture paradigm is seemingly secure. Perimeter networks – those that rely on the perimeter of security zones – distinguish between a trusted network (e.g. corporate network, internal), a demilitarized zone (DMZ) and an intrinsically insecure zone (external). Within the trusted network, the assumption is that every user, device and message that has been successfully authenticated can be trusted.
This assumption is false, as the consistency of similar successful attacks demonstrates: Based on a combination of different methods including CSS, CSRF, injections, phishing etc., malware is able to enter the trusted network and form a gateway. The attacker introduces a remote access tool (RAT) into the network, then moves laterally within the network until they can access higher privileges and find usable data.
As a result, the perimeter security approach not only contributes to uncertainty among consumers, but most significantly among service providers. They are systematically used as intermediaries for attacks on consumers and service providers. Faster product releases of apps and libraries, which allow for far greater abstract programming, massively increase complexity, reduce transparency, and thus security.
TECHNOLOGICAL EMANCIPATION/SOVEREIGNTY
Security Architectures: Perimeter vs. Zero Trust Approach
There would be no problem with perimeter networks in a static world – “static” in the sense that all end points of the network are not subject to greater dynamism. In reality, the end points are constantly changing, and end users and technical users are bringing new smartphones and IoT devices (or agents) into networks. The applications and tools posted around them, e.g. as IDEs, libraries, DevOps toolchains, change at an even faster rate than the endpoints. This dynamism results in a far greater number of systematic errors and opens up points of weakness for attackers. At the opposite end of the network, which is considered to be safe, the same people still sit and follow a link or open an attachment.
In contrast, in the case of the Zero Trust Network Architecture, the entire network is considered insecure, there is no internal secure privileged network, only an external insecure network. Threats are assumed to be a constant feature of the network. Every user, device and data flow must be authenticated, authorized and encrypted. Access to the network therefore no longer depends on localization in an internal network, rather solely on the state and credentials of the end device as well as the credentials of the user. The decision to reauthenticate and authorize is based on a dynamic set of regulations combining a variety of factors rather than a single static threshold, such as a euro amount, current location or registered address.
Zero Trust Networks use existing technologies in new ways, incorporating changes, meaning that there is no need for new protocols, libraries or languages. Alphabet/Google is an example of a pioneer in terms of Zero Trust Networks, as this company bundles these activities in its affiliate, BeyondCorp, and has been responsible for its own infrastructure (including employees) since 2014. Apple can be viewed as a Zero Trust Network with its significantly stricter closed system of closely tied iPhones and iOS for all end users.
Regulatory Authorities: Direct Regulation of IT and Technology
In addition to this paradigmatic change in terms of security architecture, the regulatory authority is strengthening the security of user data by introducing several legislative initiatives. With the IT Security Act (IT-SiG), the German legislator has implemented the European guideline for ensuring high network and information security (NIS-RL). Since June 30, 2017, IT-SiG has applied to all seven so-called “critical sectors”, including the financial and insurance sectors as well as those of information technology and telecommunication. In particular, the European Payment Services Directive II (PSD) increases the security of user data when it comes to electronic payments – as of September 14, 2019, the RTS SCA must comply with the latest safety-related element of PSD II.
Similar to PSD II, IT-SiG requires a state-of-the-art minimum level of IT security as well as a system for reporting pending serious security incidents or those that have already occurred. The requirement to report these incidents is common to both laws.
The General Data Protection Regulation will come into force as from late May. The GDPR is the first data protection law that seeks to ensure data protection by requiring technical security measures. Article 32 of the GDPR requires adequate consideration of the state of technology when it comes to implementing appropriate organizational and technical measures – an “encryption” of personal data is dedicated to every user. For the first time, GDPR can provide sanctions for the effective enforcement of data protection; with fines of up to 4% of annual turnover – up to a maximum of 20 million euros.
With the introduction of the “data protection through technology and privacy-friendly default setting” (Article 25), the GDPR also sets requirements in terms of product development and implementation – privacy by design/ privacy by default. Furthermore, the rights of the persons affected outlined in Articles 15 to 20 of the GDPR, such as the right to have data forgotten or the right to data portability, constitute non-trivial technical requirements for service providers. The ePrivacy Regulation sets out the details of the GDPR in the field of electronic communication and extends the data protection regulation to so-called “over-the-top communication providers” (OTT) such as instant messaging. To date, only traditional telecommunications providers are subject to the regulations. However, this no longer suffices as it does not offer an adequate level of protection due to the increased importance of OTTs. It is unlikely that the ePrivacy Regulation will come into force until 2019. The final content of the last of the four relevant laws cannot yet be conclusively reported, but the current trilogy shows the emergence of a trend in “pro-data privacy”.
As a result, the four regulations will increase the IT security and privacy of user data through the implementation of technical measures.
Service Providers: Gaining Reach through Technological Collaboration
Purely digital players (GAFAs) have numerous advantages as service providers: Their solutions are widely used, set standards when it comes to user convenience, and are well-versed in adapting to the latest technology paradigms. However, as their business models are largely based on collecting, evaluating and exploiting user data, they may only have limited interest (genetically and structurally) in transferring the sovereignty over this data to the user.
On the other hand, traditional analog market participants have recognized that it can be beneficial to increase their previously limited focus on data in the context of the transformation of their business models. They work together in order to generate maximum reach on the basis of technology, and are increasingly inclined to focus on lifestyle as well as function.
With regard to data, they can credibly develop solutions which do not leave data sovereignty in the hands of the user (they are not domiciled in digital space anyway), but rather return the users their sovereignty by way of their data. This involves the prerequisite of creating transparency and ensuring security.
Synthesis
Digital identity is set to experience further enhancement and economic exploitation. The sovereignty over individual digital identity thus becomes a major issue for users, as they wish to continue to preserve their data sovereignty as is the case in the analog world.
Stakeholders involved must provide users with the appropriate means in order for them to be able maintain their data sovereignty. One of the tools of choice is secure technology; major providers have recognized this and are adapting their security architectures to new, dynamic IT. Regulators and supervisory bodies are now supporting this technological approach to the solution in the form of numerous legislative initiatives aimed at achieving data security and data protection through means of secure IT systems. It is down to providers and users to walk this path themselves.


